
Prisma Access Integration
Enable seamless integration of Prisma Access security services with Meraki networks
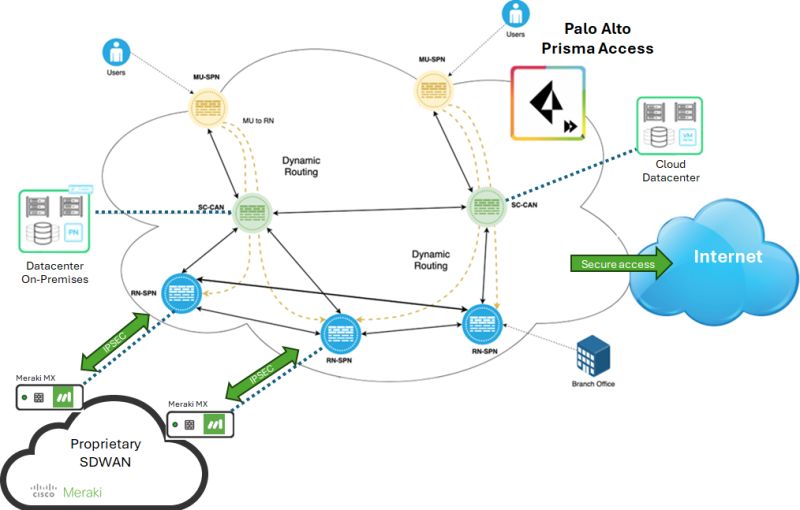
Palo Alto Prima Access offers a security stack solution from the cloud for internet and SaaS connections. Prisma acts as a secure web gateway where 0.0.0.0/0 traffic will be routed for inspection and enforcement prior to internet termination.
This document describes how to configure Prisma Access IPsec peering with the Meraki MX Security Appliance (MX/Z platforms).
Prisma Access Configuration
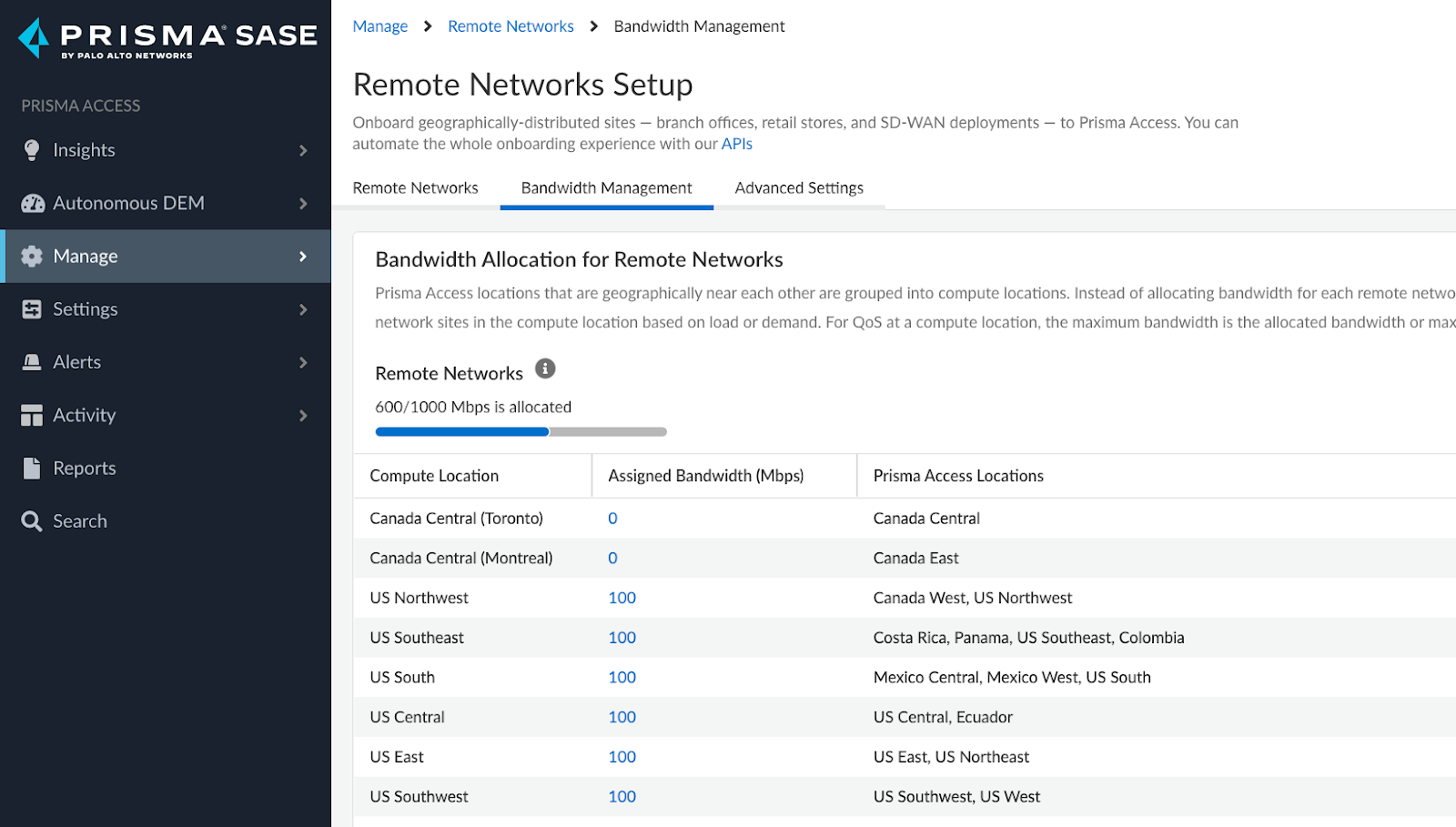
Allocate bandwidth to the required Compute locations.
Navigate to Manage > Service Setup > Remote Networks and click on Bandwidth Management tab.
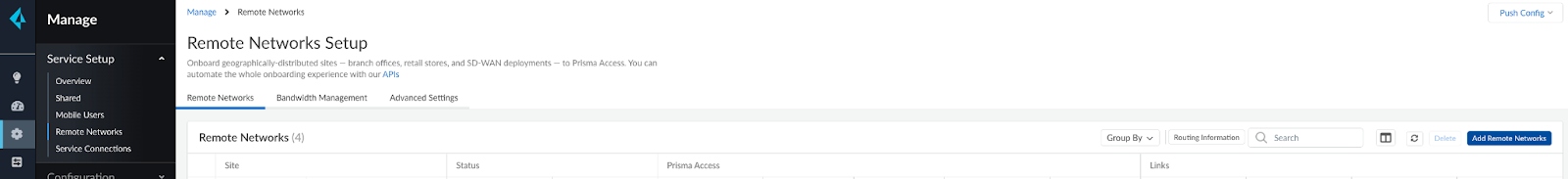
Onboard your Remote Network by Navigating to Manage > Service Setup > Remote Networks
Click “Add Remote Networks” at the top right corner
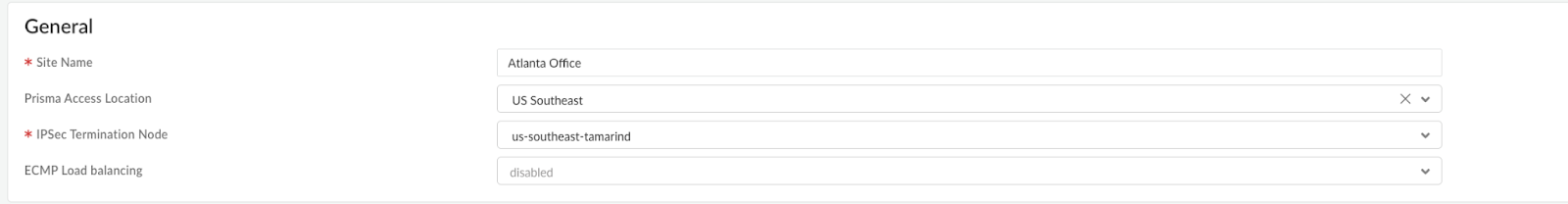
Configure General information - Select Compute point closest to your location. Below we have selected US Southeast for our Atlanta Branch Office
Setup Primary Tunnel
Update Tunnel Name, Shared secret and Address of the branch network (Static or dynamic). If the branch device does not have a dedicated IP, you can use the dynamic option with FQDN of the branch
IKE and IPsec settings can be configured by clicking on IKE Advanced Options & IPsec Advanced options
IKE Advanced Options > “Create New” and save configuration once parameters have been set.
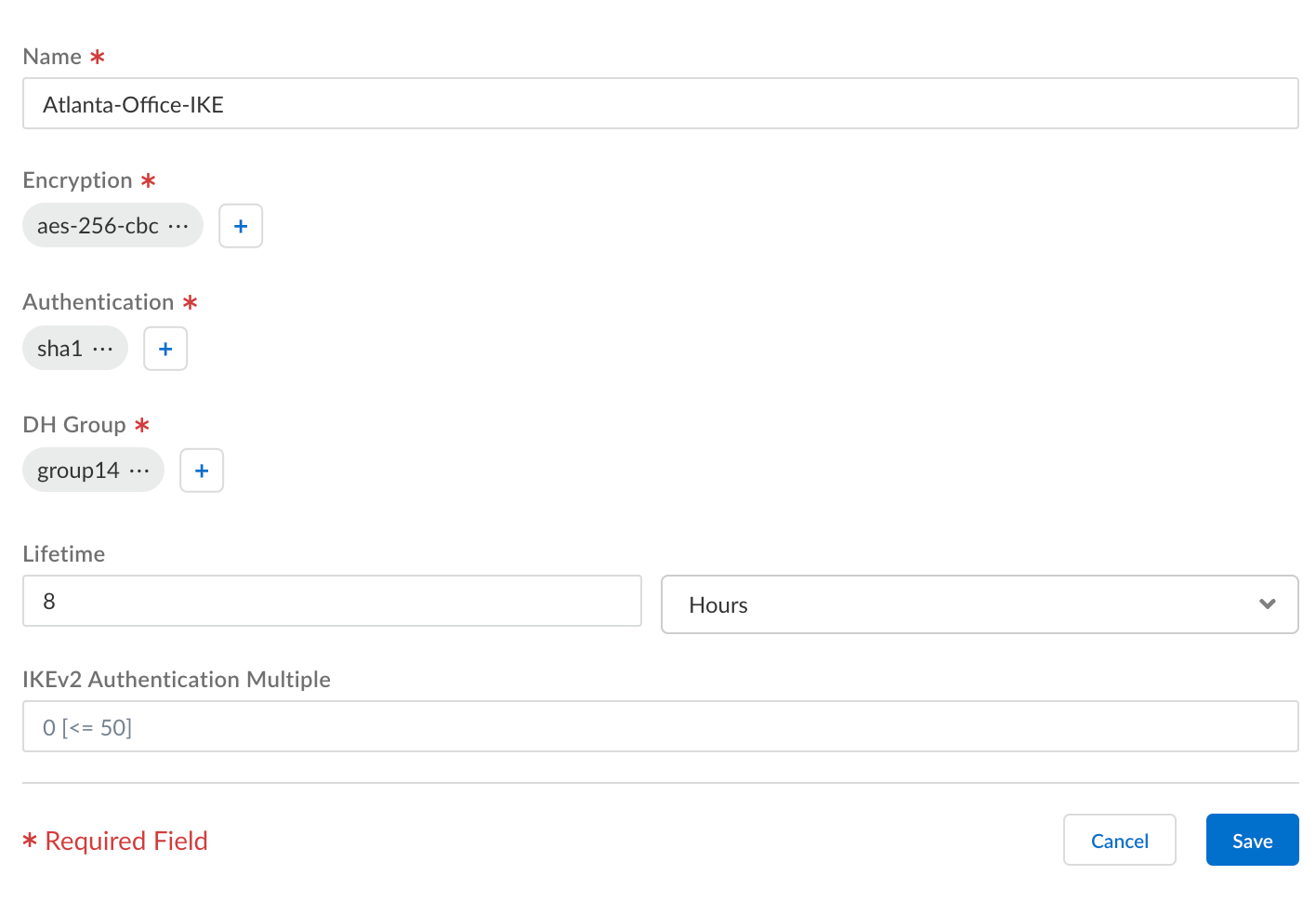
Enable Meraki site-to-site VPN
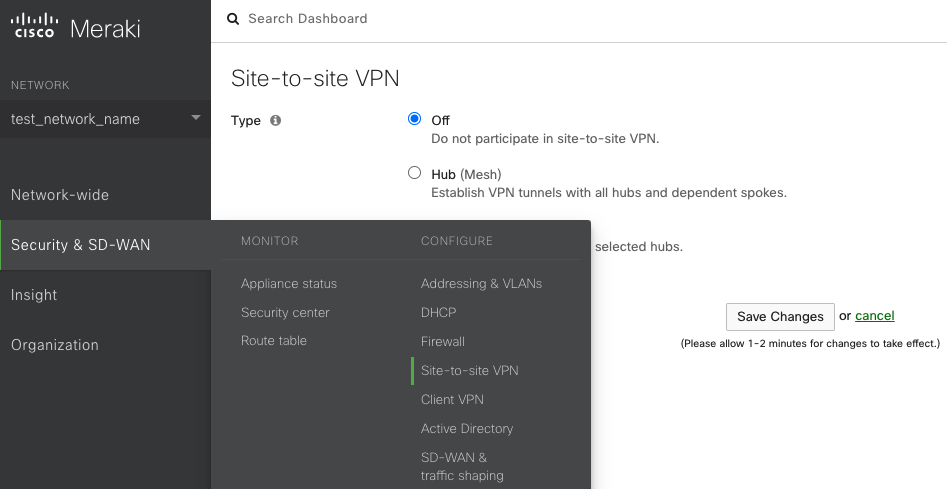
Auto VPN Topology Configuration
There are three options for configuring the MX-Z's role in the Auto VPN topology:
- Off: The MX-Z device will not participate in site-to-site VPN.
- Hub (Mesh): The MX-Z device will establish VPN tunnels to all remote Meraki VPN peers that are also configured in this mode, as well as any MX-Z appliances in hub-and-spoke mode that have the MX-Z device configured as a hub.
- Spoke: This MX-Z device (spoke) will establish direct tunnels only to the specified remote MX-Z devices (hubs). Other spokes will be reachable via their respective hubs unless blocked by site-to-site firewall rules.
Recommendation: Select Hub (Mesh) to enable AutoVPN, as this is the recommended configuration for MX peering with the IPsec VPN Peer/Prisma Access.
MX-Z Auto VPN Configuration Options
Packet Capture Options for MX/Z Platforms
The following options are available when performing a packet capture on MX/Z devices:
- Appliance: The appliance on which the capture will be performed.
- Interface: Choose the interface to run the capture on. Interface names vary by appliance configuration. Examples include:
- Internet 1 or Internet 2: Capture traffic on an active WAN uplink. Internet 2 will only appear if a second WAN link is present.
- LAN: Captures traffic from all LAN ports.
- Cellular: Captures traffic from the integrated cellular interface (not applicable to USB modems).
- Site-to-Site VPN: Captures AutoVPN traffic (MX/Z to MX/Z only). Not applicable to IPsec VPN peers.
- Output: Choose how to display capture results — view output or download as
.pcap. - Verbosity: Select the detail level of packet capture (only applies when viewing output directly in Dashboard).
- Ignore: Optionally skip broadcast/multicast traffic during capture.
- Filter Expressions: Apply custom capture filters to refine results.
Tip: To capture specific VPN phases, select the WAN interface and use the following filters:
UDP 500for Phase 1UDP 4500for Phase 2
