Cisco Meraki Solutions: Branch Networking
Revolutionized distributed branch networking
Built from the ground up for multi-site networks, Cisco Meraki products have revolutionized distributed branch networking. Zero-touch deployments, multi-site visibility and control, and automated alerts make deploying, securing, and centrally managing branch networks a breeze.
Centralized multi-site management via the cloud
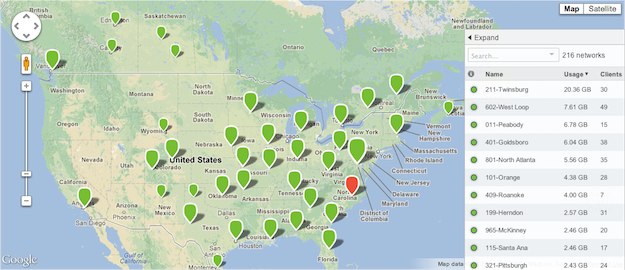
The Cisco Meraki cloud-managed architecture enables plug and play branch deployments and provides centralized visibility and control across any number of distributed locations.
Since Cisco Meraki networks are managed entirely through the Cisco Meraki web-based dashboard, configuration and diagnostics can be performed remotely just as easily as they can be performed on-site, eliminating costly field visits.
Zero-touch remote site deployment
Cisco Meraki devices self-provision, enabling branch deployments without on-site IT.
Each device downloads its configuration via the Cisco Meraki cloud, applying your network and security policies automatically so you don’t have to provision on-site. Wireless APs optimize their RF configuration based on the environment, and switches integrate seamlessly into existing RSTP domains.
Adding new sites to a network takes minutes, not hours or days, and there’s no need to train additional staff to monitor or manage the remote networks.
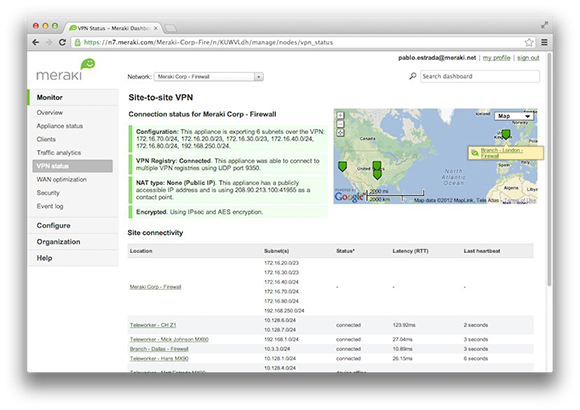
Self-provisioning VPN networks
Cisco Meraki’s unique auto provisioning site-to-site VPN connects branches securely with complete simplicity. Using IPsec over any wide area network, MX Security Appliances seamlessly link your branches to headquarters and to one another.
Site-to-site connectivity is established through a single click in the Cisco Meraki dashboard. Gone are the configuration headaches of traditional site-to-site VPNs: route discovery, authentication, and security policies are all handled automatically from the cloud. Full- and split-tunnel VPNs are configured with a single drop-down, and new sites are added with a few simple clicks.
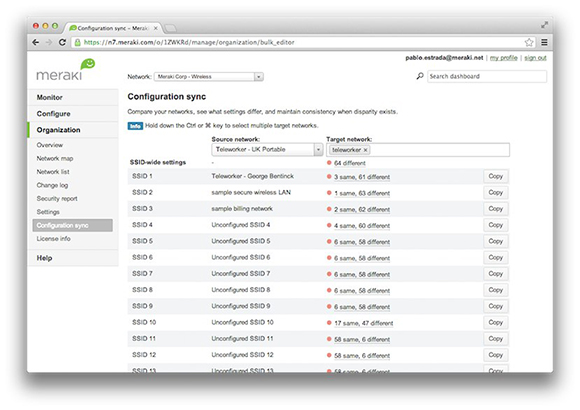
Configuration sync via network tags
Managing deployments of hundreds or thousands of networks is simplified by the dashboard. Administrators can tag networks based on region, usage, type, or any parameter to organize networks. Searching for a group of networks is as simple as searching for a tag, easing the burden of monitoring and configuration for organizations that have large, distributed deployments.
Network configurations can be copied among multiple networks, and tagging simplifies bulk configuration edits across large deployments. Simply choose source and destination networks, and the network settings to be synchronized.
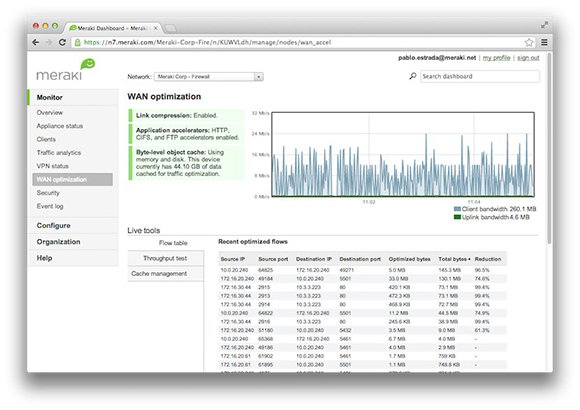
Built-in WAN Optimization
Built-in WAN optimization reduces branch bandwidth consumption and accelerates CIFS, FTP, HTTP, and TCP traffic by up to 209X over un-optimized links.
A state-of-the-art WAN optimization engine uses advanced algorithms, deduplication, compression, and hard-disk based caching to make the WAN feel like a LAN.
Cisco Meraki’s WAN optimization aids in server consolidation and private cloud initiatives, as well as any distributed network where end user bandwidth costs or performance are a priority. Enable WAN optimization on the MX with just two clicks - without new appliances, training, or overlay systems.
Secure teleworker connectivity
Cisco Meraki’s Teleworker VPN solution creates a secure IPsec tunnel from any Internet-connected Cisco Meraki wireless access point to your corporate network, providing secure remote access to IP PBX systems, file shares, and internal applications.
Client VPN securely connects mobile users through standards-based IPsec on Windows, Mac, iOS, and Android devices, without per-user licensing or cumbersome client-side software agents.

Control over applications, users, and devices
Cisco Meraki cloud-managed networking was purpose-built for distributed, multi-use networks, providing extensive visibility and control over users, content, and applications at any location. Far beyond simple host- and port-based solutions, Layer 7 fingerprinting classifies evasive and encrypted applications including P2P.
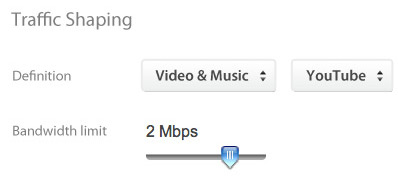
Block unwanted web traffic with CIPA-compliant content filtering, throttle bandwidth hogs like Netflix and BitTorrent, and even prioritize productivity apps like VoIP.
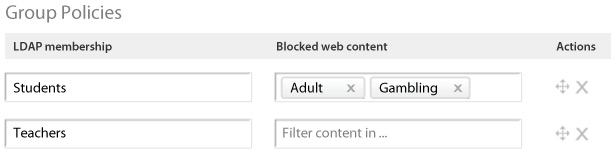
Cisco Meraki also provides insight into the users on the network, identifying clients by device type (e.g., iPads) and even username. Inspect, throttle, or block users, and integrate with Active Directory to apply different policies to different classes of users.
Manage switch fabric across branches
Built-in cloud management delivers dramatic savings in managing switch infrastructure across multiple locations. There's no need to visit each location, log into switch consoles, and manually perform switch maintenance. Reassign VLANs, enable PoE, and even enable or disable groups of ports with a few simple clicks.
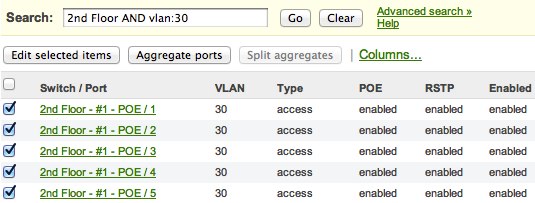
Real time remote diagnostic tools
Built-in tools deliver remote diagnostic information in real time. Monitor RF conditions, measure ping and throughput performance, and identify active clients or ports - all right through the dashboard. You can even block clients from accessing the network with a single click.
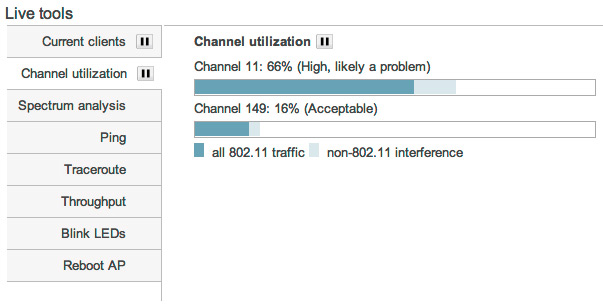
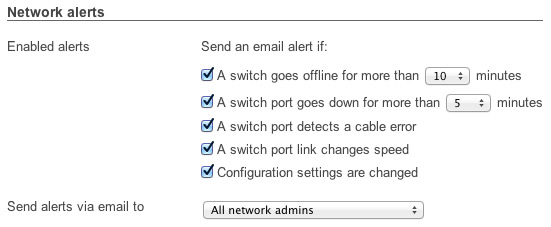
Automated monitoring and alerts
Each Cisco Meraki device is automatically monitored from the cloud, with continuous testing for WAN connectivity, latency, and more. The Cisco Meraki dashboard notifies you of problems via email alerts, and provides rich web-based diagnostics to troubleshoot your network from any web browser.
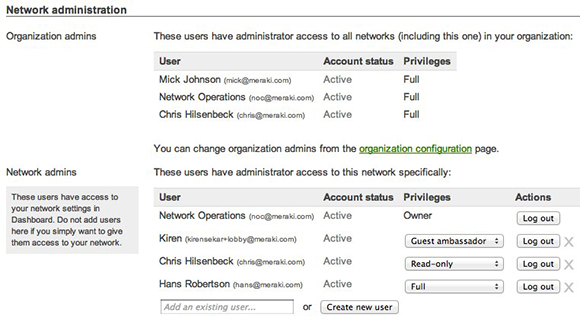
Role-based administration
Role-based administration lets administrators appoint personnel for specific subsets of an organization, providing read-only access to reports and troubleshooting tools, guest access control via the Cisco Meraki Guest Ambassador, or full access to configuration changes on the network. Additionally, the dashboard keeps logs of the time, IP, and approximate location (city, state) of logged in administrators. Role-based administration reduces the chance of accidental or malicious misconfiguration and restricts errors to isolated parts of the network.
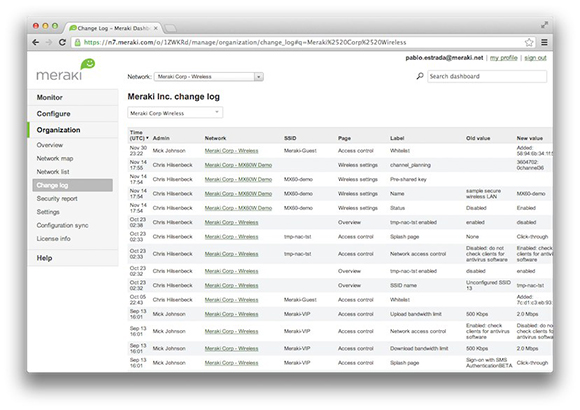
Change log with search
A searchable configuration change log indicates what configuration changes were made, who they were made by, and in which part of the organization the change occurred. Auditing configuration and login information provides greated visibility into your network and keeps records of events as required by security standards and best-practices.
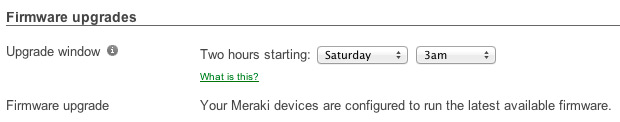
Seamless firmware updates
Firmware updates are delivered seamlessly from the cloud to Cisco Meraki devices. When firmware updates are available, an administrator simply schedules an appropriate time for devices to download and install the new version, eliminating insecure and out of date firmware.
Maintain compliance with security requirements without deciphering compatibility matrices, performing time consuming manual updates, or visiting branch locations to upgrade hardware.