
Cisco Meraki MR33
Entry-level, cloud-managed 802.11ac wireless

Sorry, this product is no longer available, Please contact us for a replacement.
Click here to jump to more pricing!
Please Note: All Prices are Inclusive of GST
Overview:
MR33
Dual-band, 802.11ac Wave 2 2x2:2 MU-MIMO Access Point with dedicated security and RF management radio as well as integrated Bluetooth Low Energy beacon and scanning radio
Entry-level cloud-managed 802.11ac wireless
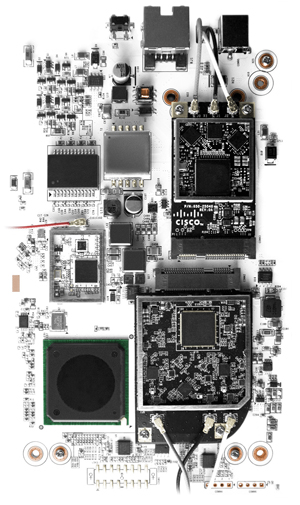
The Cisco Meraki MR33 is a quad-radio, cloud-managed 2x2:2 802.11ac Wave 2 access point with MU-MIMO support. Designed for next-generation deployments in offices, schools, hospitals, shops, and hotels, the MR33 provides performance, enterprise-grade security, and simple management.
The MR33 provides a maximum 1.3 Gbps* aggregate frame rate with concurrent 2.4 GHz and 5 GHz radios. A dedicated third radio provides real-time WIDS/WIPS with automated RF optimization. An integrated Bluetooth Low Energy (BLE) radio delivers beacon and scanning capabilities.
The combination of cloud management, 802.11ac Wave 2, full-time RF environment scanning, and integrated Bluetooth technology delivers the throughput, reliability, and flexibility required by demanding business applications like voice and high-definition streaming video, today and tomorrow.
MR33 and Meraki Cloud Management: A Powerful Combination
The MR33 is managed through the Meraki cloud, with an intuitive browser-based interface that enables rapid deployment without training or certifications. ince the MR33 is self-configuring and managed over the web, it can even be deployed at a remote location without on-site IT staf
The MR33 is monitored 24x7 via the Meraki cloud, which delivers real-time alerts if the network encounters problems. Remote diagnostics tools enable real- me troubleshooting over the web, meaning multi-site, distributed networks can be managed remotely.
The MR33's firmware is always kept up to date from the cloud. New features, bug fixes, and enhancements are delivered seamlessly over the web, meaning no anual software updates to download or missing security patches to worry about.
MR33 Highlights
- General use wireless
Hardware features
- 3 radios: 2.4 GHz, 5 GHz, and dual-band WIDS/WIPS
- 2-stream 802.11ac and 802.11n, up to 1.2 Gbps
- Integrated BLE radio
- 2x2 MU-MIMO 802.11ac Wave 2
- Up to 1.3 Gbps aggregate dual-band frame rate
- 802.3af PoE compatible
Cloud management
- Network-wide visibility and control
- Self-provisioning for rapid deployment
- Automatic reporting
- Seamless firmware updates
Enterprise security
- 802.1X integration
- Air Marshal: real-time WIPS with forensics
- Stateful Layer 3-7 firewall
- Identity-based group policies
- Built-in antivirus scan (NAC)
Guest access
- 1-click secure guest access
- Guest isolation firewall
- Customizable splash pages
- Dual-concurrent, 2-stream MIMO radios
- Third radio dedicated to security and RF management
- Built-in real-time RF spectrum view
- Cloud-based automatic RF optimization
Layer 7 traffic shaping
- Classify hundreds of applications automatically
- Create per-application bandwidth limits
- Prioritize productivity apps
- Restrict recreational traffic
Mesh
- Self-configuring, self-optimizing mesh
- High performance multi-radio routing protocols
- Extends coverage to hard-to-wire areas
- Self-heals after cable or switch failures
Device management
- Create device-specific firewall rules
- Deploy applications and updates
- Troubleshoot issues with built-in RDP
Features:
Aggregate data rate of up to 1.3 Gbps*
A 5 GHz 2x2:2 radio supporting 80 MHz channel widths and a 2.4 GHz 2x2:2 radio supporting 40 MHz channel widths offer a combined dual-radio aggregate frame rate of 1.3 Gbps*, with up to 866 Mbps in the 5 GHz band thanks to 802.11ac Wave 2 and 400 Mbps in the 2.4 GHz band.
Multi User Multiple Input Multiple Output (MU-MIMO)
With support for the 802.11ac Wave 2 standard, the MR30H offers MU-MIMO for more effcient transmission to multiple clients. Especially suited for enviroments with numerous mobile devices, MU-MIMO enables multiple clients to receive data simultanously. This increases the total network perfomance and the improves the end user experience.
Dedicated third radio delivers 24x7 wireless security and RF analytics
The MR30H's sophisticated, dedicated dual-band third radio scans the environment continuously, characterizing RF interference and containing wireless threats like rogue access points. No more need to choose between wireless security, advanced RF analysis, and serving client data: a dedicated third radio means that all three occur in real-time, without any impact to client traffic or AP throughput.
Bluetooth Low Energy beacon and scanning
An integrated Bluetooth low energy radio provides seamless deployment of BLE beacon functionality and effortless visibility of BLE devices within range of the AP. The MR30H enables the next generation of location-aware applications and engagement right out of the box.
Automatic cloud-based RF optimization
The MR30H's sophisticated, automated RF optimization algorithms use a dedicated third radio to collect real-time, full-spectrum RF analysis data - which is continuously fed back to the Meraki cloud. The Meraki cloud then automatically tunes the MR30H's channel selection and transmit power for optimal performance under the most challenging RF conditions.
Secure wireless environments using 24x7 Air Marshal
No longer choose between a wireless intrusion prevention system (WIPS) and serving client data: thanks to the dedicated third radio, Air Marshal, a highly optimized built-in WIPS, scans continuously for threats and remediates them as commanded, all without disrupting client service. Alarms and optional auto- ontainment of rogue APs are configured via flexible remediation policies, ensuring optimal security and performance in even the most challenging wireless environments.
Integrated enterprise security and guest access
The MR30H features integrated, easy-to-use security technologies to provide secure connectivity for employees and guests alike. Advanced security features such as AES hardware-based encryption and WPA2-Enterprise authentication with 802.1X provide wire-like security while still being easy to configure. One-click guest isolation provides secure, Internet-only access for visitors. Our policy firewall (Identity Policy Manager) enables group or devicebased, granular access policy control. Meraki Teleworker VPN makes it easy to extend the corporate LAN to remote sites, without requiring all clients and devices to have client VPN software. PCI compliance reports check network settings against PCI requirements to simplify secure retail deployments.
Application-aware traffic shaping
The MR30H includes an integrated layer 7 packet inspection, classification, and control engine, enabling you to set QoS policies based on traffic type. Prioritize your mission critical applications, while setting limits on recreational traffic, e.g., peer-to-peer and video streaming.
Voice and Video optmizations
Industry standard QoS features are easy to configure like Wireless Multi Media (WMM) Access Categories, 802.1p, and DSCP.
Low-profile, sleek, and compact design
Despite its robust feature set, the MR30H is packaged in a sleek, low-profile enclosure that blends seamlessly into any environment.
Self-configuring, self-optimizing, self-healing
When plugged in, the MR30H automatically connects to the Meraki cloud, downloads its configuration, and joins the appropriate network. The MR30H then self-optimizes, determining the ideal channel, transmit power, and client connection parameters. As necessary, it will also self-heal, responding automatically to switch failures and other errors.
*Refers to maximum over-the-air data frame rate capability of the radio chipset, and may exceed data rates allowed by IEEE Std 802.11ac-compliant operation.
Solutions:
MR Cloud Managed Wireless Access Points
The Meraki MR series is the world's first enterprise-grade line of cloud-managed WLAN access points. Designed for challenging enterprise environments, the MR access points use advanced 802.11ac and 802.11n technologies including MIMO, beam forming and channel bonding to deliver the throughput and reliable coverage required by demanding business applications.
Centralized Cloud Management
The award-winning Cisco Meraki cloud management architecture provides powerful and intuitive centralized management, while eliminating the cost and complexity of traditional on-site wireless controllers. Seamlessly manage campus-wide WiFi deployments and distributed multi-site networks with zero-touch access point provisioning, network-wide visibility and control, cloud-based RF optimization, seamless firmware updates and more. With an intuitive browser-based user interface, Meraki WLANs configure in minutes without training or dedicated staff. Adding new sites to a network takes minutes, not hours or days, and there's no need to train additional staff to monitor or manage the remote networks. Meraki devices self-provision, enabling large campus and multi-site deployments without on-site IT.
Class-Leading Enterprise Features
Cisco Meraki access points are built from the highest grade components and carefully optimized for a seamless user experience. The outcome: faster connections, greater user capacity, more coverage, and fewer support calls.
![]()
Built for Performance
Enterprise-class 802.11ac and 802.11n APs feature high power radios and enhanced receive sensitivity. MIMO and integrated beamforming maximize capacity without sacrificing range.
- Enhanced CPU for line-rate deep packet inspection
- Flash memory provisioned for cloud management
- Custom RF design for enhanced performance
![]()
Dedicated Security Radio
In addition to the high-power 2.4 GHz and 5 GHz client-serving radios, the Meraki MR34 packs a dedicated security radio. The radio:
- Continuously scans and protects against security threats
- Senses the RF environment and adapts to interference
- Automatically configures RF settings to maximize performance
Rapid Deployment and Scalability
Built from the ground up for multi-site networks, Meraki access points have revolutionized distributed branch wireless networking. Zero-touch deployments, multi-site visibility and control, and automated alerts make deploying, securing, and centrally managing branch networks a breeze.
The Meraki cloud-managed architecture enables plug and play branch deployments and provides centralized visibility and control across any number of distributed locations. Since Meraki MR series APs are managed entirely through the Meraki web-based dashboard, configuration and diagnostics can be performed remotely just as easily as they can be performed on-site, eliminating costly field visits. Each device downloads its configuration via Meraki's cloud, applying your network and security policies automatically so you don't have to provision them on-site.
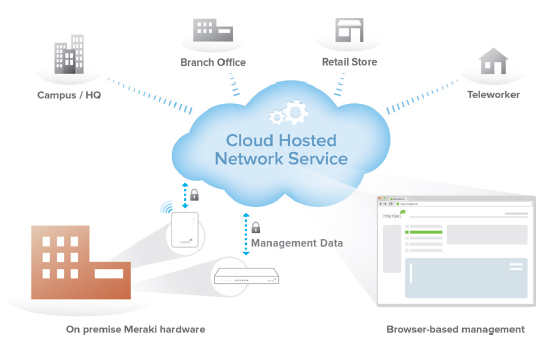
Meraki Cloud Management Architecture
High Performance RF Design
Every Meraki access point continuously and automatically monitors its surroundings to maximize WiFi performance. By measuring channel utilization, signal strength, throughput, signals from non-Meraki APs, and non-WiFi interference, Meraki APs automatically optimize WiFi performance of individual APs and maximize system-wide performance.
Meraki APs have been deployed and proven in the most demanding environments, supporting more than 100 users per AP and collectively serving hundreds of Megabits per second of user traffic to thousands of devices. By eliminating traditional hardware controllers, Meraki also eliminates the performance bottleneck that often chokes high-density wireless deployments.
By measuring utilization from neighboring APs, detecting WiFi signals from non-Meraki APs, and identifying non-WiFi interference, Meraki APs continuously stay on top of changing and challenging conditions. Tools such as real-time spectrum analysis and live channel utilization deliver immediate information on the RF environment at any part of the network. Even in dynamic environments, Meraki networks automatically detect and adapt to interference from non-WiFi sources.
Real-time and historical metrics ensure maximum system-wide performance. Wireless channels, AP output power, and client connection settings are automatically adapted to changing performance and interference conditions, eliminating the need for tedious manual adjustment of dozens of independent parameters.
Mesh networking, included in every Meraki AP, extends coverage to hard to wire areas and creates a self-healing network that is resilient to cable and switch failures, continuing to operate despite failures or configuration changes in the rest of the network, without the need for manual configuration or optimization.
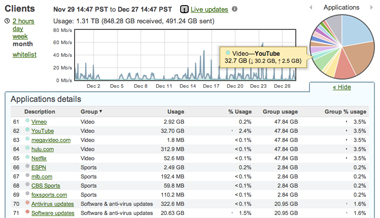
User Analytics and Traffic Shaping
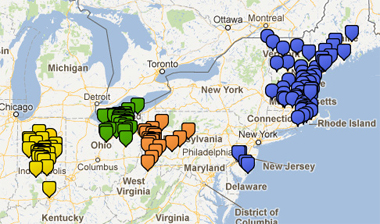
Multi-Site Management
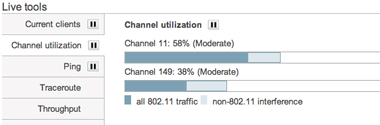
Live Troubleshooting Tools
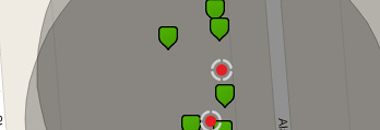
Air Marshal: Real-Time Wireless Intrusion Prevention System
Enterprise Security and a Dedicated Radio
The MR series comes equipped with complete out-of-the-box enterprise class security. Segment wireless users, applications, and devices; secure your network from attacks and enforce the right policies for each class of users. A built-in stateful policy firewall, 802.1X/RADIUS support, and native Active Directory integration deliver fine-grained access control, while a guest access firewall provides secure, Internetonly guest WiFi in just one click. Integrated network access control (NAC) provides end-user anti-virus scanning for accurate client device posture asessment to protect your wired and wireless network against virus infections.
Indoor APs feature a radio dedicated to full-time scanning, rogue AP containment, and automatic RF optimization. With Air Marshal, it is possible to set up a real-time wireless intrusion detection and prevention system (WIDS/WIPS) with user-defined threat remediation policies and intrusion alarms, enabling secure wireless environments without complex setup or systems integration. Auto RF eliminates the need for manual RF configuration by scanning the environment for utilization, interference, and other metrics, and computing the optimal channel and power settings for every AP in the network. Meraki WLANs are fully HIPAA and PCI compliant.
Built-in Guest Access
Meraki cloud management provides the ability to customize and integrate splash pages onto each Meraki MR access point, with options for click-through or sign-on splash using your own RADIUS server or the Meraki cloud-based RADIUS user database. The Meraki MR series features a complete array of built-in captive portal tools, including a guest ambassador portal for new-user sign-on, splash sign-in tracking, application blocking and traffic shaping, free and paid tiers of access, integrated credit-card processing and prepaid codes generation, and splash by-pass for corporate-issued or recognized devices.
The Entire Network Under A Single Pane Of Glass
Powerful and intuitive multi-site management via the cloud, while eliminating the cost and complexity of traditional on-site wireless controllers.
The industry's only end-to-end solution which unifies WAN, LAN, wireless LAN, and mobile device management under a single pane of glass.
Meraki Mobile App
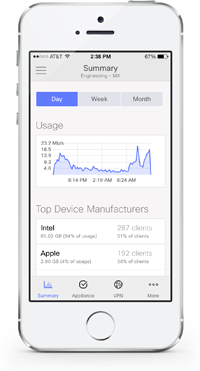 The Meraki dashboard mobile app, available for iOS and Android, is ideal for network management on the go.
The Meraki dashboard mobile app, available for iOS and Android, is ideal for network management on the go.
Monitor
Manage your entire Meraki infrastructure from anywhere
- Monitor wireless, switching, and security infrastructure
- See network status and usage
- Receive push notifications for network outages
Speed Deployments
- Scan AP barcode to add it to your network
- Use the phone's camera to photograph the AP mounting location
- Pinpoint the AP location using GPS
Troubleshoot Remotely
- Verify connectivity using live tools
- Measure network throughput remotely
- Reboot devices without on-site staff
CMX
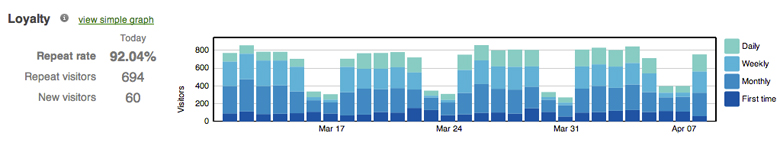
The Meraki MR series tracks probing MAC addresses from associated and non-associated clients. This data is exported in real time from the access points to Meraki's cloud for analytics; information is then calculated and then presented in the Meraki dashboard to display metrics such as user dwell-time, repeat visits and capture rate (people passing by vs. coming inside a site). This information can be used by retailers, hospitality, and enterprise customers to understand foot traffic and visitor behavior across sites, and can facilitate an optimization of opening hours, marketing initatives, and staffing policies.
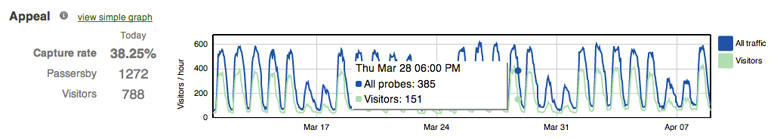
CMX Location Analytics (for non-associated clients)
BYOD-ready, Out of the Box
User-owned devices have exploded onto networks everywhere, with new iPads, Androids, and smartphones connecting every day. Meraki MR series APs feature built-in support for BYOD and make it easier than ever to securely track and support user-owned iPads, tablets, smartphones, and laptops - without extra appliances, licenses, or complex VLAN configurations. Using integrated Layer 7 client fingerprinting, client devices are automatically identified and classified, letting you distinguish between iPads and iPhones, device operating systems, and even manufacturer. Device-specific policies can be automatically applied to restrict, quarantine, or throttle userowned devices. Client fingerprinting combined with a heuristicsdriven reporting engine allows you to generate detailed reports of BYOD clients that have connected, measure the bandwidth and applications they've accessed, and even see their percentage of total traffic. Bonjour forwarding facilitates seamless discovery of Apple devices across VLANs, rounding out a full BYOD-centric feature set.
Complete with a free mobile device management (MDM) client agent called Systems Manager, monitor each of your organization's devices, showing useful metrics including client hardware/software information and recent location, and centrally manage your corporate devices with a great degree of granulaity; log in with remote desktop or command-line, push new applications, and remotely lock and erase devices.
Client Location Tracking
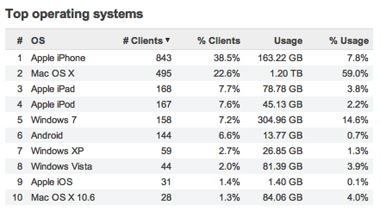
Device Reporting and Analytics
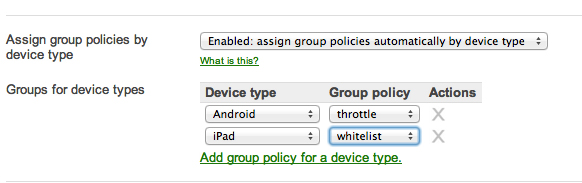
Device-Based Group Policies
Auto-Tunneling VPN Technology
Leveraging the Meraki cloud architecture, site-to-site VPNs can be enabled via a single click without any command-line configurations or multi-step key permission setups; Meraki cloud management automatically tunnels, hole punches, and configures devices to eliminate the complexity seen in traditional VPN setups. Complete with IPsec encryption, deploy the following architectural setups within minutes:
- Teleworker VPN: Securely extend the corporate LAN to remote sites wirelessly, using the MR series with your own server or a Meraki MX
- Site-to-site VPN: Multi-branch VPN w/ WAN optimization and Content Filtering (using Meraki MX Security Appliance)
- Secure roaming: Layer 2 and layer 3 roaming for large campus environments
Distributed Packet Processing
Meraki devices execute packet processing at the edge. Each wireless access point features a high performance CPU that enforces layer 3-7 firewall policies, application QoS, network access control (NAC), and more. Meraki networks scale seamlessly: add capacity by simply deploying more APs, without concern for controller bottlenecks or choke points.
Every Meraki wireless access point is built with the packet processing resources to secure and control its client traffic, without need for a wireless LAN controller. Meraki APs are built with a high performance CPU, hardware-accelerated encryption, and extended memory resources to implement stateful firewall policies, voice and video optimization, and even layer 7 traffic classification and QoS.
Cloud Management:
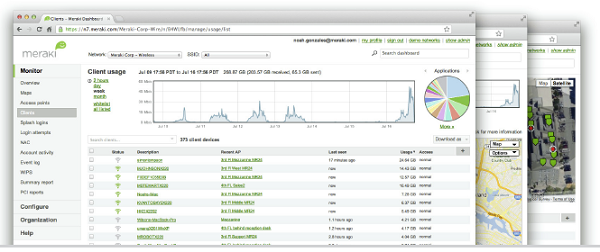
Cisco Meraki's cloud based management provides centralized visibility & control over Cisco Meraki's wired & wireless networking hardware, without the cost and complexity of wireless controllers or overlay management systems. Integrated with Cisco Meraki's entire product portfolio, cloud management provides feature rich, scalable, and intuitive centralized management for networks of any size.
Highlights
- Unified visibility and control of the entire network via a single dashboard: wireless, switching, and security appliances
- Streamlines large networks with tens of thousands of endpoints
- Zero-touch provisioning for rapid deployment
- Built-in multi site network management tools
- Automated network monitoring and alerts
- Intuitive interface eliminates costly training or added staff
- Network tagging engine - search and sync settings by tag
- Role-based administration and auditable change logs
- Continuous feature updates delivered from the cloud
- Highly available and secure (PCI / HIPAA compliant)
Cloud Managed Networks
Cisco Meraki's hardware products are built from the ground up for cloud management. As a result, they come out of the box with centralized control, layer 7 device and application visibility, real time web-based diagnostics, monitoring, reporting, and much more.
Cisco Meraki networks deploy quickly and easily, without training or dedicated staff. Moreover, Cisco Meraki provides a rich feature set that provides complete control over devices, users, and applications, allowing for flexible access policies and rich security without added cost or complexity.
Cisco Meraki's cloud management provides the features, security, and scalability for networks of any size. Cisco Meraki scales from small sites to campuses, and even distributed networks with thousands of sites. Cisco Meraki devices, which self-provision via the cloud, can be deployed in branches without IT. Firmware and security signature updates are delivered seamlessly, over the web. With the cloud, branches can automatically establish secure VPN tunnels between one another with a single click.
With a secure, PCI and HIPAA compliant architecture and fault tolerant design that preserves local network functionality during WAN outages, Cisco Meraki is field proven in high security and mission critical network applications.
Cloud Management Architecture
Cisco Meraki's architecture provides feature rich network management without on-site management appliances or WiFi controllers.
Every Cisco Meraki device - including wirelesss access points, Ethernet switches, and security appliances - connects over the Internet to Cisco Meraki's datacenters, which run Cisco Meraki's cloud management platform. These connections, secured via SSL, utilize a patented protocol that provides real time visibility and control, yet uses minimal bandwidth overhead (typically 1 kbps or less.)
In place of traditional command-line based network configuration, Cisco Meraki provides a rich web based dashboard, providing visibility and control over up to tens of thousands of Cisco Meraki devices, anywhere in the world. Tools, designed to scale to large and distributed networks, make policy changes, firmware updates, deploying new branches, etc. simple and expedient, regardless of size or location. Cisco Meraki's real time protocols combine the immediacy of on-premise management applications with the simplicity and centralized control of a cloud application.
Every Cisco Meraki device is engineered for cloud management. Specifically, this means that Cisco Meraki devices are designed with memory and CPU resources to perform packet processing, QoS, layer 3-7 security, encryption, etc. at the network edge. As a result, no network traffic passes through the cloud, with the cloud providing management functionality out of the data path. This architecture enables networks to scale horizontally, adding capacity simply by adding more endpoints, without concern for centralized bottlenecks or chokepoints. Equally important, since all packet processing is performed on premise, end-user functionality is not compromised if the network's connection to the cloud is interrupted.
Cisco Meraki's cloud platform is designed to spread computation and storage across independent server clusters in geographically isolated datacenters. Any server or datacenter can fail without affecting customers or the rest of the system. Additionally, Cisco Meraki's datacenter design is field proven to support tens of thousands of endpoints.
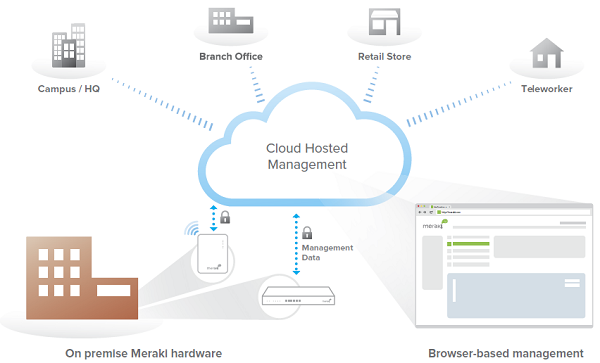
Cloud Management Architecture
Powerful Insight and Troubleshooting Tools
Cisco Meraki's cloud architecture delivers powerful insight and includes live tools integrated directly into the dashboard, giving instant analysis of performance, connectivity, and more. Using live tools, network administrators no longer need to go on site to perform routine troubleshooting tests. Visibility into devices, users, and applications gives administrators the information needed to enforce security policies and enable the performance needed in today's demanding network environments.
Troubleshooting tools such as ping, traceroute, throughput, and even live packet captures are integrated directly into the Cisco Meraki dashboard, dramatically reducing resolution times and enabling troubleshooting at remote locations without on-site IT staff.
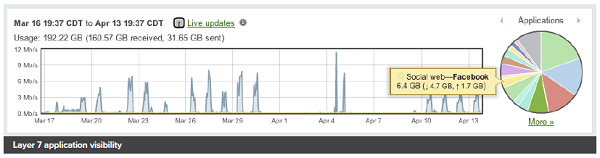
Layer 7 application visibility
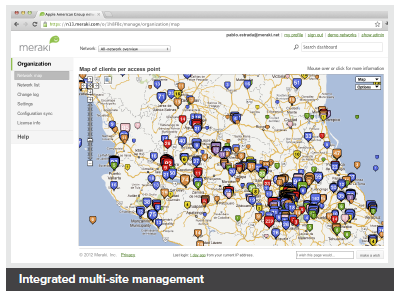
Integrated multi-site management
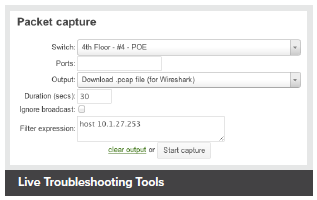
Live Troubleshooting Tools
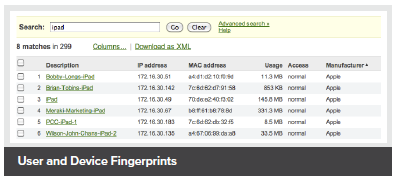
User and Device Fingerprints
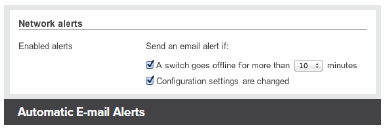
Automatic E-mail Alerts
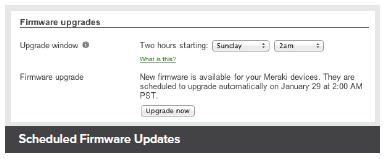
Scheduled Firmware Updates
Out-of-Band Control Plane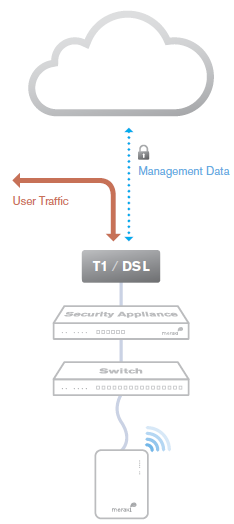
Cisco Meraki's out-of-band control plane separates network management data from user data. Management data (e.g., configuration, statistics, monitoring, etc.) flows from Cisco Meraki devices (wireless access points, switches, and security appliances) to Cisco Meraki's cloud over a secure Internet connection. User data (web browsing, internal applications, etc.) does not flow through the cloud, instead flowing directly to its destination on the LAN or across the WAN.
Advantages of an out of band control plane:
Scalability
- Unlimited throughput: no centralized controller bottlenecks
- Add devices or sites without MPLS tunnels
- Add switching capacity without stacking limitations
Reliability
- Redundant cloud service provides high availability
- Network functions even if management traffic is interrupted
Security
- No user traffic passes through Cisco Meraki's datacenters
- Fully HIPAA / PCI compliant
What happens if a network loses connectivity to the Cisco Meraki cloud?
Because of Cisco Meraki's out of band architecture, most end users are not affected if Cisco Meraki wireless APs, switches, or security appliances cannot communicate with Cisco Meraki's cloud services (e.g., because of a temporary WAN failure):
- Users can access the local network (printers, file shares, etc.)
- If WAN connectivity is available, users can access the Internet
- Network policies (firewall rules, QoS, etc.) continue to be enforced
- Users can authenticate via 802.1X/RADIUS and can roam wirelessly between access points
- Users can initiate and renew DHCP leases
- Established VPN tunnels continue to operate
- Local configuration tools are available (e.g., device IP configuration)
While Cisco Meraki's cloud is unreachable, management, monitoring, and hosted services are temporarily unavailable:
- Configuration and diagnostic tools are unavailable
- Usage statistics are stored locally until the connection to the cloud is re-established, at which time they are pushed to the cloud
- Splash pages and related functionality are unavailable
Cisco Meraki Datacenter Design
Cisco Meraki's cloud management service is colocated in tier-1, SAS70 type II certified datacenters. These datacenters feature state of the art physical and cyber security and highly reliable designs. All Cisco Meraki services are replicated across multiple independent datacenters, so that customer-facing services fail over rapidly in the event of a catastrophic datacenter failure.
- Five geographically dispersed datacenters
- Every customer's data (network configuration and usage metrics) replicated across three independent datacenters
- Real-time data replication between datacenters (within 60 seconds)
- Nightly archival backups
Availability Monitoring
- 24x7 automated failure detection - all servers are tested every five minutes from multiple locations
- Rapid escalation procedures across multiple operations teams
- Independent outage alert system with 3x redundancy
Disaster Recovery
- Rapid failover to hot spare in event of hardware failure or natural disaster
- Out of band architecture preserves end-user network functionality, even if connectivity to Cisco Meraki's cloud services is interrupted
- Failover procedures drilled weekly
Cloud Services Security
- 24x7 automated intrusion detection
- Protected via IP and port-based firewalls
- Access restricted by IP address and verified by public key (RSA)
- Systems are not accessible via password access
- Administrators automatically alerted on configuration changes
Physical Security
- High security card keys and biometric readers control facility access
- All entries, exits, and cabinets are monitored by video surveillance
- Security guards monitor all traffic into and out of the datacenters 24x7, ensuring that entry processes are followed
- Only configuration and usage statistics are stored in the cloud
- End user data does not traverse through the datacenter
- All sensitive data (e.g., passwords) stored in encrypted format
Disaster Preparedness
- Datacenters feature sophisticated sprinkler systems with interlocks to prevent accidental water discharge
- Diesel generators provide backup power in the event of power loss
- UPS systems condition power and ensure orderly shutdown in the event of a full power outage
- Each datacenter has service from at least two top-tier carriers
- Seismic bracing for raised floor, cabinets, and support systems
- In the event of a catastrophic datacenter failure, services fail over to another geographically separate datacenter
Environmental Controls
- Over-provisioned HVAC systems provide cooling and humidity control
- Flooring systems are dedicated for air distribution
Certification
- Cisco Meraki datacenters are SAS70 type II certified
- PCI level 1 certified
Security Tools for Administrators
In addition to Cisco Meraki's secure out-of-band architecture and hardened datacenters, Cisco Meraki provides a number of tools for administrators to maximize the security of their network deployments. These tools provide optimal protection, visibility, and control over your Cisco Meraki network.
Two-factor authentication
Two-factor authentication adds an extra layer of security to an organization's network by requiring access to an administrator's phone, in addition to her username and password, in order to log in to Cisco Meraki's cloud services. Cisco Meraki's two factor authentication implementation uses secure, convenient, and cost effective SMS technology: after entering their username and password, an administrator is sent an a one-time passcode via SMS, which they must enter before authentication is complete. In the event that a hacker guesses or learns an administrator's password, she still will not be able to access the organization's account, as the hacker does not have the administrator's phone. Cisco Meraki includes two-factor authentication for all enterprise users at no additional cost.Password policies
Organization-wide security policies for Cisco Meraki accounts help protect access to the Cisco Meraki dashboard. These tools allow administrators to:
- Force periodic password changes (e.g., every 90 days)
- Require minimum password length and complexity
- Lock users out after repeated failed login attempts
- Disallow password reuse
- Restrict logins by IP address
Role-based administration
Role-based administration lets supervisors appoint administrators for specific subsets of an organization, and specify whether they have read-only access to reports and troubleshooting tools, administer managed guest access, or can make configuration changes to the network. This minimizes the chance of accidental or malicious misconfiguration, and restricts errors to isolated parts of the network.Configuration change alerts
The Cisco Meraki system can automatically send human-readable email and text message alerts when configuration changes are made, enabling the entire IT organization to stay abreast of new policies. Change alerts are particularly important with large or distributed IT organizations.Configuration and login audits
Cisco Meraki logs the time, IP, and approximate location (city, state) of logged in administrators. A searchable configuration change log indicates what configuration changes were made, who they were made by, and which part of the organization the change occurred in.SSL certificates
Cisco Meraki accounts can only be accessed via https, ensuring that all communication between an administrator's browser and Cisco Meraki's cloud services is encrypted.Idle Timeout
30 seconds before being logged out, users are shown a notice that allows them to extend their session. Once time expires, users are asked to log in again.
Specifications:

| MR32 Specifications | |
|---|---|
| Radio |
|
| Operating Bands |
|
| 802.11ac & 802.11n Capabilities |
|
| Power |
|
| Mounting |
|
| Physical Security |
|
| Environment |
|
| Physical Dimensions | 8.5" x 4.3" x 1.3" (215 mm x 110 mm x 32 mm), not including deskmount feet or mount plate |
| Weight | Weight: 13.2 oz (376.5 g) |
| Antenna | Integrated omni-directional antennas (3.8 dBi gain at 2.4 GHz, 3.9 dBi gain at 5 GHz) |
| Interfaces |
|
| Security |
|
| Quality of Service |
|
| Mobility |
|
| LED Indicators |
|
| Warranty | Lifetime hardware warranty with advanced replacement included |
RF Performance Table:
| Operating Band | Operating Mode | Data Rate | TX Power (dBm) | RX Sensitivity |
|---|---|---|---|---|
| 2.4 GHz | 802.11b | 1 Mb/s 2 Mb/s 5.5 Mb/s 11 Mb/s |
20dBm 20dBm 20dBm 20dBm |
-96 dBm -93 dBm -81 dBm -89 dBm |
| 2.4 GHz | 802.11g | 6 Mb/s 9 Mb/s 12 Mb/s 18 Mb/s 24 Mb/s 36 Mb/s 48 Mb/s 54 Mb/s |
20dBm 20dBm 20dBm 19dBm 19dBm 18dBm 18dBm 18dBm |
-91 dBm -90 dBm -88 dBm -87 dBm -84 dBm -81 dBm -76 dBm -75 dBm |
| 2.4 GHz | 802.11n(HT20) | MCS0/8 MCS1/9 MCS2/10 MCS3/11 MCS4/12 MCS5/13 MCS6/14 MCS7/15 |
20/20 dBm 20/20 dBm 19/19 dBm 19/19 dBm 18/18 dBm 18/18 dBm 18/18 dBm 18/18 dBm |
-91/91 dBm -88/-88 dBm -85/-85 dBm -82/-82 dBm -79/-79 dBm -75/-75 dBm -73/-73 dBm -70/-70 dBm |
| 2.4 GHz | 802.11ac(VHT20) | MCS0/0 MCS1/1 MCS2/2 MCS3/3 MCS4/4 MCS5/5 MCS6/6 MCS7/7 MCS8/8 |
20/20 dBm 20/20 dBm 19/19 dBm 19/19 dBm 18/18 dBm 18/18 dBm 18/18 dBm 18/18 dBm 17/17 dBm |
-90/-90 dBm -88/-88 dBm -85/-85 dBm -83/-83 dBm -81/-81 dBm -79/-79 dBm -76/-76 dBm -72/-72 dBm -70/-70 dBm |
| 2.4 GHz | 802.11n(HT40) | MCS0/8 MCS1/9 MCS2/10 MCS3/11 MCS4/12 MCS5/13 MCS6/14 MCS7/15 |
20/20 dBm 20/20 dBm 19/19 dBm 19/19 dBm 18/18 dBm 18/18 dBm 18/18 dBm 18/18 dBm |
-89/-89 dBm -86/-86 dBm -84/-84 dBm -82/-82 dBm -77/-77 dBm -73/-73 dBm -71/-71 dBm -70/-70 dBm |
| 2.4 GHz | 802.11ac(VHT40) | MCS0/0 MCS1/1 MCS2/2 MCS3/3 MCS4/4 MCS5/5 MCS6/6 MCS7/7 MCS8/8 MCS9/9 |
20/20 dBm 20/20 dBm 19/19 dBm 19/19 dBm 18/18 dBm 18/18 dBm 18/18 dBm 18/18 dBm 17/17 dBm 16/16 dBm |
88/-88 dBm -86/-86 dBm -83/-83 dBm -81/-81 dBm -78/-78 dBm -75/-75 dBm -71/-71 dBm -68/-68 dBm -65/-65 dBm -63/-63 dBm |
| 5 GHz | 802.11a | 6 Mb/s 9 Mb/s 12 Mb/s 18 Mb/s 24 Mb/s 36 Mb/s 48 Mb/s 54 Mb/s |
21dBm 21dBm 20dBm 20dBm 20dBm 20dBm 20dBm 20dBm |
-90dBm -87dBm -86dBm -85dBm -84dBm -79dBm -74dBm -71dBm |
| 5 GHz | 802.11n(HT20) | MCS0/8 MCS1/9 MCS2/10 MCS3/11 MCS4/12 MCS5/13 MCS6/14 MCS7/15 |
21/21 dBm 21/21 dBm 20/20 dBm 20/20 dBm 20/20 dBm 20/20 dBm 20/20 dBm 19/19 dBm |
-88/-88 dBm -85/-85 dBm -83/-83 dBm -79/-79 dBm -76/-76 dBm -72/-72 dBm -71/-71 dBm -69/-69 dBm |
| 5 GHz | 802.11n(VHT20) | MCS0/0 MCS1/1 MCS2/2 MCS3/3 MCS4/4 MCS5/5 MCS6/6 MCS7/7 MCS8/8 |
21/21 dBm 21/21 dBm 20/20 dBm 20/20 dBm 20/20 dBm 20/20 dBm 20/20 dBm 19/19 dBm 18/18 dBm |
-88/-88 dBm -86/-86 dBm -83/-83 dBm -79/-79 dBm -77/-77 dBm -75/-75 dBm -72/-72 dBm -70/-70 dBm -67/-67 dBm |
| 5 GHz | 802.11n(HT40) | MCS0/8 MCS1/9 MCS2/10 MCS3/11 MCS4/12 MCS5/13 MCS6/14 MCS7/15 |
21/21 dBm 21/21 dBm 20/20 dBm 20/20 dBm 19/19 dBm 19/19 dBm 19/19 dBm 19/19 dBm |
-85/-85 dBm -84/-87 dBm -84/-84 dBm -79/-79 dBm -77/-77 dBm -72/-72 dBm -70/-70 dBm -68/-68 dBm |
| 5 GHz | 802.11n(VHT40) | MCS0/0 MCS1/1 MCS2/2 MCS3/3 MCS4/4 MCS5/5 MCS6/6 MCS7/7 MCS8/8 MCS9/9 |
21/21 dBm 21/21 dBm 20/20 dBm 20/20 dBm 19/19 dBm 19/19 dBm 19/19 dBm 19/19 dBm 18/18 dBm 17/17 dBm |
-85/-85 dBm -82/-82 dBm -79/-79 dBm -77/-77 dBm -74/-74 dBm -70/-70 dBm -68/-68 dBm -67/-67 dBm -64/-64 dBm -63/-63 dBm |
| 5 GHz | 802.11ac(VHT80) | MCS0/0 MCS1/1 MCS2/2 MCS3/3 MCS4/4 MCS5/5 MCS6/6 MCS7/7 MCS8/8 MCS9/9 |
20/20 dBm 20/20 dBm 19/19 dBm 19/19 dBm 18/18 dBm 18/18 dBm 18/18 dBm 18/18 dBm 17/17 dBm 17/17 dBm |
-83/-83 dBm -81/-81 dBm -79/-79 dBm -76/-76 dBm -73/-73 dBm -70/-70 dBm -67/-67 dBm -66/-66 dBm -62/-62 dBm -60/-60 dBm |
Signal Coverage Pattern:
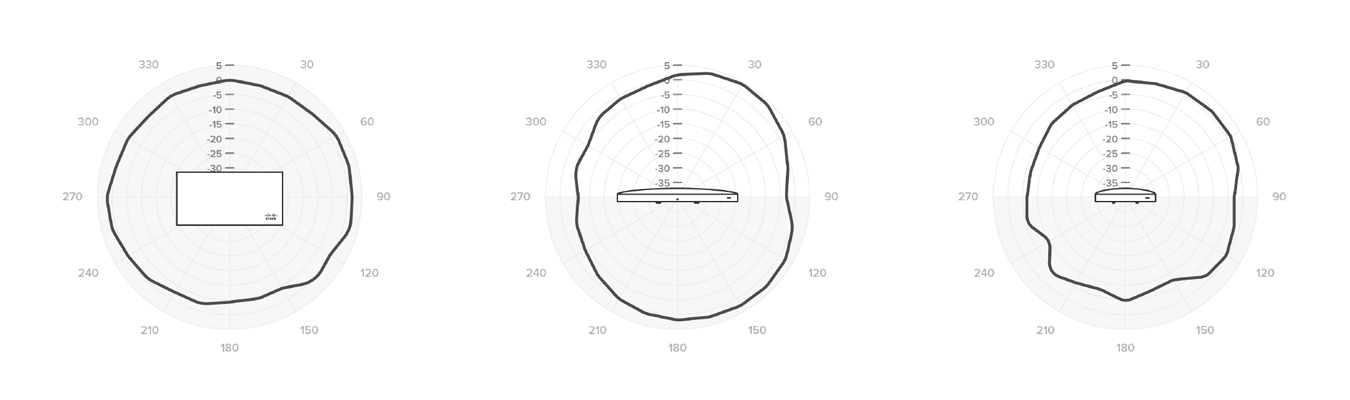
Radiation Pattern for 2.4GHz Antennas
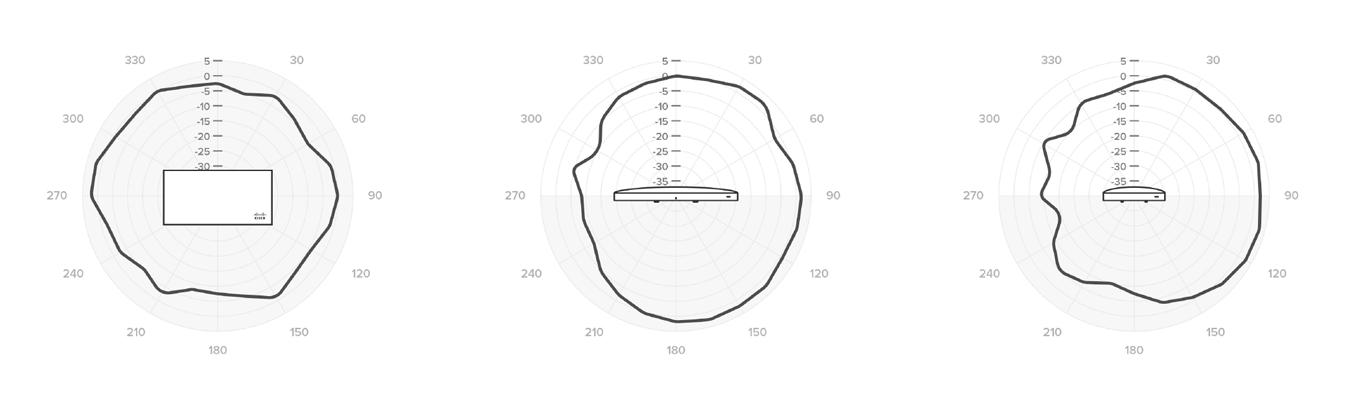
Radiation Pattern for 5GHz Antennas
Compare Access Points:
Documentation:
Download the Cisco Meraki MR33 Datasheet (PDF).
Download the Cisco Meraki MR Family Datasheet (PDF).
Pricing Notes:
- All Prices are Inclusive of GST
- Pricing and product availability subject to change without notice.
Our Price: Request a Quote
Our Price: Request a Quote
Our Price: Request a Quote
Our Price: Request a Quote
Our Price: Request a Quote
Our Price: Request a Quote




